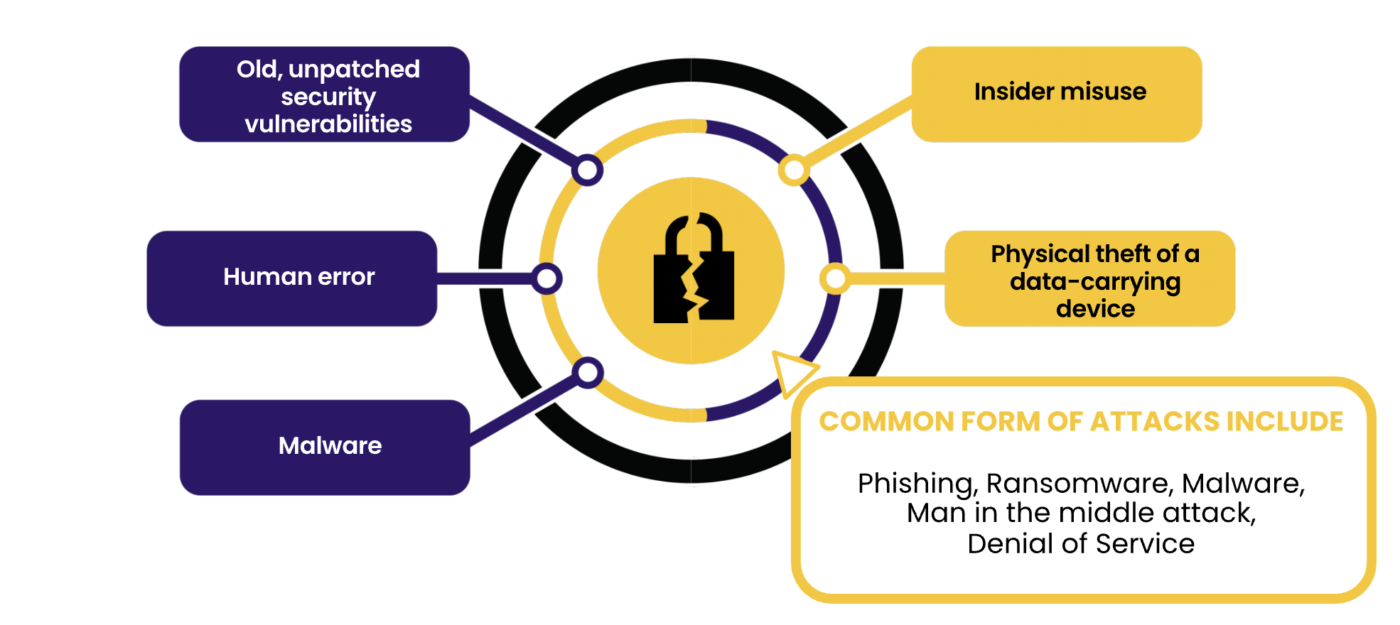
The Top 5 Reasons Businesses Get Hacked
The Top Attacks in The World
1‘TeaBot’ or ‘Anatsa’ accounts for more than 64% of mobile banking apps, or 410 injected by this malware.
2 The second most dangerous, ‘Hydra’ hidden inside the google play store and steals your mobile phone credentials.
3 ‘Godfather’ is a banking malware which has so far targeted 400 financial companies and tries to steal money transfers
4 ‘Ransomware’ in 2022 costs banks 456 million USD. Phishing costs 2.7 billion USD and is the top challenge to the
financial industry.
5 NBC in June 2023 reported 7345 cases of data theft in Cambodia in 2021. The banking sector received 21.3%.
(Khmer Times June 6, 2023)
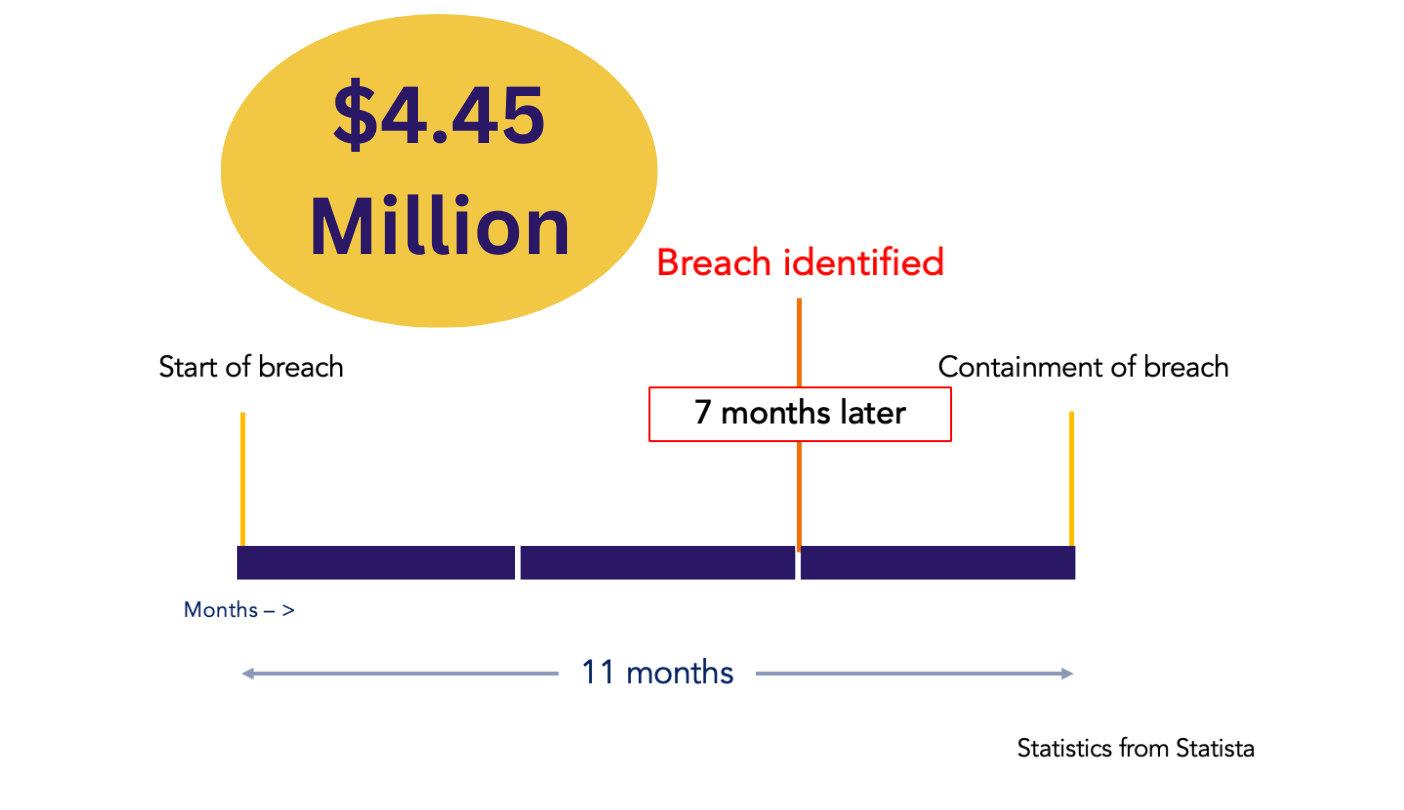
Average Cost and Lifecycle of a Security Breach
SA Mobile Application Secure
SCAN
helps financial enterprises build secure and compliant mobile applications, and it is the only unified solution that combines comprehensive threat visibility.
- Identify risks on your mobile application.
- Helps discover and fix compliance, privacy, and security issues within the development process before release of application.
- Regularly scanning as required to keep mobile application secure and compliant after each update.
- Once Yearly for regulatory compliance requirement.

SHIELD
Shield helps protect the source code, intellectual property (IP), and data from potential attacks like reverse engineering and code tampering.
- Provides source code level obfuscation to give unsurpassed protection.
- Embed robust tamper detection mechanisms and customizable defense response to prevent any attempts to attack mobile application.
- Report hacking and reversing attempts directly into security information and even management system for further analysis and action.
- Help detect and defend against device, network, phishing, and malware attacks.
- Helps enterprises gain runtime threat visibility and enables mobile apps to defend themselves against mobile attacks during runtime

ARM
ARM offers an application performance management service.
- Identify abnormal and slow API operations
- Improves the efficiency of online troubleshooting.
- Automatically identify the upstream and downstream dependencies of applications.
- Identify performance bottlenecks and abnormal calls in the system by using the application topology.
- Automatically discover and monitor common web frameworks and RPC frameworks in application code.

RESPOND
Respond, led by certified, experienced and skilled practitioners following procedures based on industry best practices (SANS, NIST, ISO).
-
PREPARE
If an incident is suspected, the client is to:
– Contact 24/7 notification centre.
– Submit incident data form.
– Monitor for further developments. -
IDENTIFY
Within 6 hours:
– Acknowledge notification; respond to customer.
Within 6 – 48 hours
– Ascertain event validity and severity.
– Deploy agents) to suspected compromised endpoints.
– Begin data collection.
Within 48 hours:
– Conduct preliminary analysis.
– Define scope and assign roles.
– Determine and communicate action plan.
– Begin containment and remediation. -
CONTAIN, ERADICATE, RECOVER
Beyond 48 hours:
– Contain/Quarantine the incident.
– Conduct root cause analysis.
– Confirm/Deny data exfiltration.
– Extended remediation.
– Recover lost data (where possible).
– Restore normal business operations.
– Submit initial assessment report. -
LESSONS LEARNED
Final report will cover:
– Cause of breach
– Methodology used.
– Remediating actions.
– Recommendations to improve security posture.













